Introduction
Our job during an investigation is to reconstruct the most complete picture of an incident with the evidence we have. Often we find ourselves in a position missing a tiny piece of the puzzle. Finding that piece can make all the difference to the investigation and outcome for the client.
What is RDP Bitmap Cache
You’re probably familiar with Remote Desktop Protocol (RDP). It is a tool commonly used by system administrators to administer machines remotely. Threat actors love RDP, too, and often leverage it to move laterally within an environment. Why do they choose RDP? Well often there are no controls to limit RDP connections, and it provides a graphical user interface (GUI) as if they were sitting right in front of the machine.
Here is where it starts to get interesting. When a user initiates a RDP session, the originating machine stores copies of portions of the remote display during the session. This is known as the RDP Bitmap Cache. The primary purpose of the RDP Bitmap Cache is to improve performance during RDP sessions and reduce potential lag. Instead of constantly streaming the entire display over the network, the RDP client reuses the cache images.
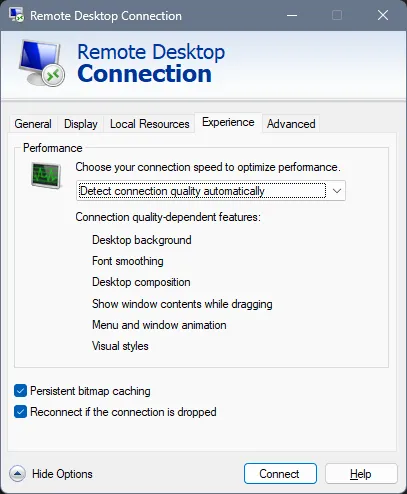
By default, the cache is enabled. This setting can be found within the RDP client experience settings as shown below.
Value in an Investigation
RDP Bitmap Cache contains sections of a RDP session’s remote display. Therefore it may reveal activities a Threat Actor performed on a system such as applications, files viewed and commands executed.
While other forensic artifacts provide evidence that a program was executed, the RDP Bitmap Cache may reveal the content of the application’s interface. The cache does not provide a complete picture, although visual clues that can help alter the course of an investigation. In an investigation where evidence of data exfiltration is limited to identifying sections of a file transfer utilities GUI may reveal items such as the exfiltration IP address and the data exfiltrated. This could ultimately add significant value to a client during an investigation allowing early e-discovery, notification and potentially even a successful takedown.
Considerations
As with all forensic artifacts, there are considerations and caveats. Sadly, RDP Bitmap Cache will not give you everything you need. There are two main limitations of RDP Bitmap Cache:
- Incomplete View: The cache stores small bitmap fragments, not full screenshots. The cache is meant to optimise performance, not to record user activity. So while it can provide valuable hints, it will not give you a complete view of the session.
- Stored on the Originating System: The cache is stored on the machine where the RDP session originated. Where a Threat Actor connects to a network via a VPN and uses RDP from their machine you will not have access to their local machine and therefore not the cache.
While the cache can add context, especially when logs are lacking, it is only one piece of the puzzle. It’s another tool in your tool kit, but not a complete solution.
The Investigation Scenario
Let’s walk through a scenario where the cache may be valuable:
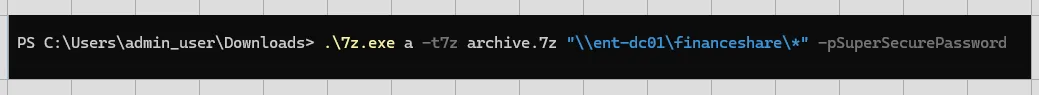
A Threat Actor has connected to a remote machine via RDP and executed a command to compress a directory using 7-Zip with a password via the command line. This is known as data staging which is a common behaviour of Threat Actors prior to data exfiltration. The environment lacks adequate logging of this command and therefore the password and compressed contents may be an unknown to the investigation.
Location
RDP Bitmap Cache is stored under the following path for Windows 7 and above operating systems:
`C:\Users\<user>\AppData\Local\Microsoft\Terminal Server Client\Cache\`In this directory, you will find files such as cache000.bin and cache001.bin. These are the bitmap cache files you’re after.
Collection of the Cache Files Using KAPE
To make the collection process smoother you can use Kroll Artifact Parser and Extractor (KAPE). This will come in handy when you need to collect data from a system remotely using an Endpoint Detection and Response (EDR) or even Velociraptor. Once you have downloaded KAPE onto the remote machine, use the below command.
.\kape.exe --tsource C: --tdest C:\Temp\Collection --target RDPCache --zip RDPCacheParsing RDP Bitmap Cache with BMC Tools
Now that we’ve got the cache files, we need to extract the bitmap images. We can achieve this with BMC Tools. Here is the process:
- Download BMC Tools from the GitHub Repository (https://github.com/ANSSI-FR/bmc-tools)
- Unzip the directory to a convenient location on your machine.
- Place the RDP Bitmap Cache files within a convenient location on your machine.
- Open a terminal and navigate to the directory containing BMC Tools.
- Use the following command to run BMC Tools and extract the images:
python .\bmc-tools.py -s <Cache files location> -d .\OutputBMC-Tools will process the cache files and extract the bitmap images, saving them in the output directory. You’ll end up with a large amount of small images each a fragment of the RDP session. Below is the output from our scenario.

Piecing the Pieces Together
Looking at thousands of tiny images puts into perspective how much of a puzzle this artifact actually is. All those hours doing puzzles for fun have come into practice.
How can we start to organise and make sense of all these images? Thankfully, the German Federal Office for Information Security has made a tool known as RDP Cache Stitcher. RDP Cache Stitcher provides a place to start piecing all the images together to hopefully get an indication of what occurred during the RDP session.
Here’s how to use it:
- Download RDP Cache Stitcher from the GitHub Repository (https://github.com/BSI-Bund/RdpCacheStitcher).
- Run the executable (RdpCacheStitcher.exe).
- Select file -> new case.
- Select the folder containing the output images.
- Start placing the images to create snippets of the RDP session display.
Handy tip: If you select a square next to a placed image RDP Cache Stitcher will suggest images that may match on the right.
Returning to our scenario with RDP Cache Stitcher we were able to piece together the command the Threat Actor used to compress and stage data. Identifying this command during an investigation could be incredibly valuable. It not only points us to the data that was staged but also reveals the password the Threat Actor used. With this information, we would be able to locate the impacted data and perform e-discovery and early notifications.
Final Thoughts
The RDP Bitmap Cache might not give you a full crystal clear image of a Threat Actor’s RDP session although It could contain the missing piece that ties everything together. Even if it’s only a small snippet, it might provide the insight needed.
Additional Resources
- BMC-Tools GitHub Repository: https://github.com/ANSSI-FR/bmc-tools
- RDP Cache Stitcher GitHub Repository: https://github.com/BSI-Bund/RdpCacheStitcher
- YouTube Tutorial on RDP Bitmap Cache Analysis: https://www.youtube.com/watch?v=9P845AMjJF0