TL;DR
Why Should I Care? Unified Audit Logs are incredibly valuable as they contain information of activities performed within M365. However, investigating Unified Audit Logs can become a very manual process.
What Should I Consider? Consider using Parse Unified Audit Logs (PUAL) to improve the process of investigating Unified Audit Logs.
Introducing Parse Unified Audit Logs (PUAL)
During a Microsoft 365 (M365) investigation, Unified Audit Logs are incredibly valuable as they contain information of activities performed within M365. However, working with these logs can become a very manual process. Usually this involves expanding JSON data from CSV outputs, enriching IP addresses and filtering the data only to start identifying suspicious activity.
With this opportunity identified, I put ChatGPT to the test and developed this handy script to help improve the process of investigating Unified Audit Logs.
Find the code within the GitHub Repo: https://github.com/DFIRinProgress/Parse-Unified-Audit-Logs-PUAL
Parse Unified Audit Logs (PUAL)
This tool is designed to support the investigation of Unified Audit Logs. The tool processes the logs, enriches IP addresses, offers filtering and provides visualizations. Happy Hunting!
[GPT assisted coding]
Features
- Data Processing: Expands JSON from audit data for analysis.
- IP Enrichment: Provides additional context for IP addresses using IPinfo.
- Filtering: Allows for filtering based on a keyword, IP address and operation.
- Visualization: Generates charts and plots for visualization of trends and patterns.
- Export: Exports parsed and filtered audit data to a CSV file.
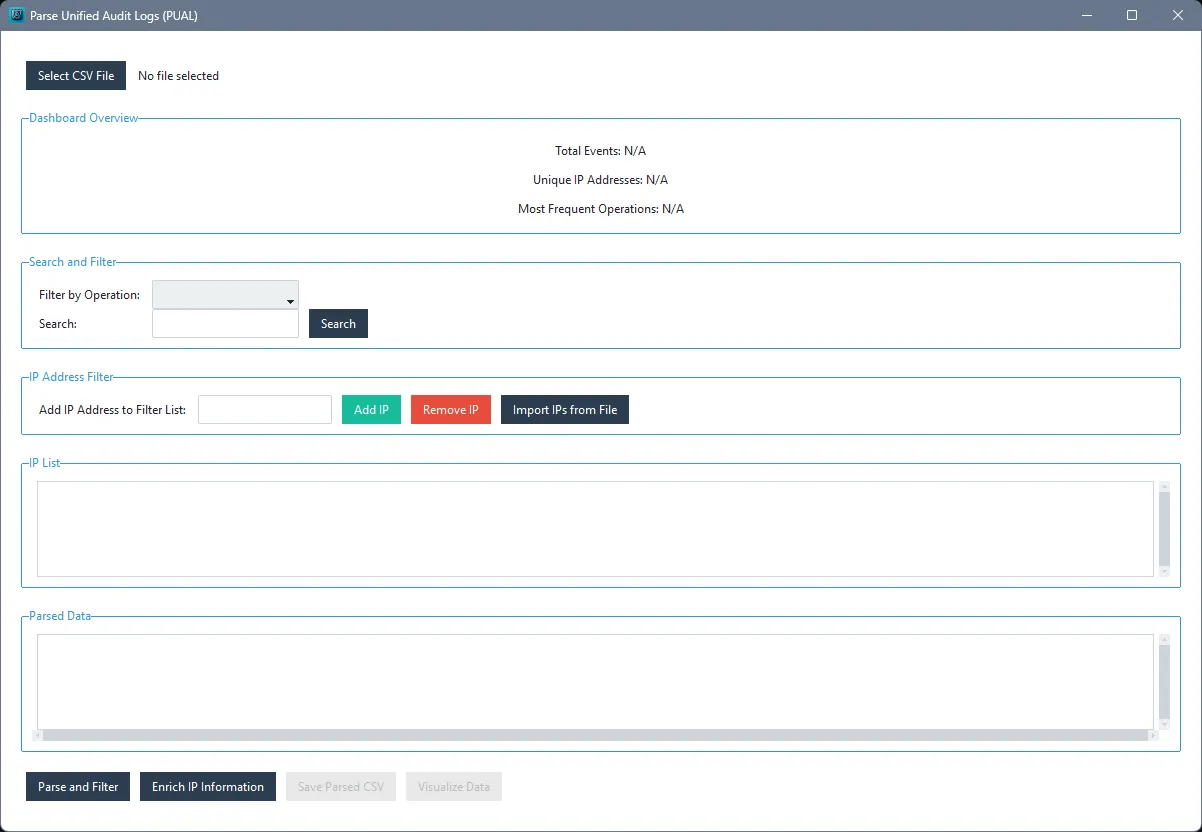
Preview
Installation
To install the required dependencies, execute the following command:
pip install -r requirements.txtNote: The Microsoft Visual C++ Redistributable is required for this tool.
Usage
Running the Tool
- In the config.json file replace “YOUR_TOKEN_HERE” with your IPinfo token.
- Start the application by executing the main script:
python .\main.pyFile Selection
- Select CSV File: Select the Unified Audit Log in CSV format. The selected file will be processed and displayed in the application.
Dashboard Overview
- Total Events: Displays the total number of events.
- Unique IP Addresses: Shows the count of unique IP addresses.
- Most Frequent Operations: Lists the most frequent operations in the log.
Search and Filter
- Filter by Operation: Use the dropdown menu to filter the audit log by specific operations.
- Search: Enter keywords to search through the logs.
Visualizations
- Operation Frequency Bar Chart: Displays the frequency of different operations.
- Client IP Distribution Pie Chart: Shows the distribution of IP addresses.
- Operation Timeline Line Plot: Illustrates the number of operations over time.
Example Usage
- Upload a Unified Audit Log file: Use the “Select CSV File” button to select your audit log.
- Parse and Filter: Use the parse and filter button to process the selected file expanding the JSON data.
- Enrich IP addresses: Use the IP enrichment feature to get additional context using IPinfo.
- Filtering and Searching: Use the search and filter options to narrow down on a specific operation, keyword or IP addresses.
- Visualizations: Visualize charts and plots to identify trends and patterns.
Contributing
If you have any suggestions for improvements or new features, please create an issue or submit a pull request on GitHub.